While device growth brings transformative effects to several industries and to people’s daily lives, it also induces an additional level of system complexity to the infrastructure that will handle device data.
In parallel, there is a strong imperative to be able to trust the data that gets acquired and acted on by IoT solutions. The effects of corrupted devices or data on systems that make instant, analytics-based decisions can have a severe cost. As a result, there is an increasing need for solutions that secure the source of data at the edge, creating end- to-end security up to the cloud.
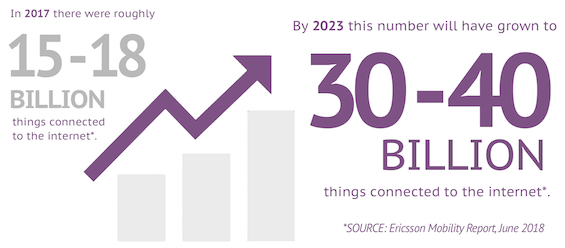
Connected devices volumes are expected to increase exponentially in the upcoming years. Analyst data seem to converge and indicate that the number of things connected to the internet should exceed the number of humans by a factor of 8 come 2020.
While this growth brings transformative effects to several industries and to people’s daily lives, it also induces an additional level of system complexity to the infrastructure that will handle device data. IoT systems need to be cognisant of a vast number of device types, interfaces, communication protocols, or device lifecycles.
In parallel, there is a strong imperative to be able to trust the data that gets acquired and acted on by IoT solutions. It is a well-known fact that Big Data is only as good, or as secure, as the small data that it is built on. The effects of corrupted devices or data on systems that make instant, analytics-based decisions can have a severe financial, material and human cost.
As a result, there is an increasing need for solutions that secure the source of data at the edge, creating end- to-end security up to the cloud, and help IoT customers simplify the overall security equation.
Fortunately, there is an extensive body of work already available detailing the security risks associated with Internet of Things systems. This document does not intend to replicate this work. Instead we will focus specifically on the security of IoT devices. We will make an effort to categorise some of the key challenges faced by IoT vendors at the edge of the network. We will also go over hardware or software solutions that can abstract a good portion of the IoT complexity from the customer. We will discuss what new use cases can be brought about by open, secure application platforms such as Java Card technology.
