Smart Card Technology and Security
The self-containment of Smart Card makes them resistant to attack as they do not need to depend upon potentially vulnerable external resources. Because of this, Smart Cards are often used in applications which require strong security protection and authentication.
Technology and security are strongly related. Crackers find sophisticated ways to get at supposedly secure data on cards => Manufacturers have to come up with more sophisticated locks and keys on cards => Crackers come up with better techniques to bypass these ... thus forming an infinite improvement loop, with both sides driving each other to use and invent better technology.
There are four different aspects of the Smart Card security:
Communication with the outside world
A Smart Card and a Card Accepting Device (CAD) communicate via means of small data packets called APDUs (Application Protocol Data Units). The following characteristics of this interaction make it harder for third parties to attack the system successfully:
Small bit rate (9600 bits per second) using a serial bi-directional transmission line (ISO standard 7816/3),
half duplex mode for sending the information (data only travels in one direction at a time)
The communication follows a sophisticated protocol, described below.
However, every external device communicating with the card makes it more vulnerable to attack via the communication link.
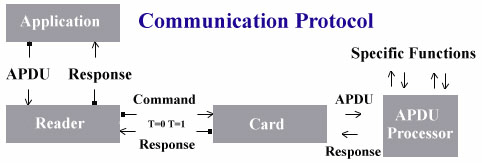
The Smart Card and the CAD use an mutual active authentication protocol to identify each other. The card generates a random number and sends it to the CAD, which encrypt the number with a shared encryption key before returning it to the card. The card then compares the returned result with its own encryption. The pair may then perform the operation in reverse.
Once communication is established, each message between the pair is verified through a message authentication code. This is a number that is calculated based on the data itself, an encryption key, and a random number. If data has been altered (for any reason, including transmission errors) message must be retransmitted. Alternatively, if the chip has sufficient memory and processing power, the data can be verified through a digital signature.
The most common encryption methods are symmetric DES (Data Encryption Standard), 3DES (triple DES) and public key RSA (Rivest-Shamir-Adleman's algorithm), allowing up 56, 168, and 1024 bit long keys, respectively. Unfortunately, these keys are not unbreakable, as explained by Ross Anderson and Markus Kuhn in their book `Design Principles for Tamper-Resistant Smart Card Processors'. The pair managed to crack the Dallas DS5002FP Secure Microcontroller, described at the time by one European signals intelligence agency as the most secure processor available on general sale. They used brute force methods on a PC enhanced with a couple of hundred dollars of extra hardware!
Cards and CADs communicate via a special instruction set. For example, the Schlumberger Reflex 60 instruction set contains:
| 0x60 | Gets reader type and activate reader |
| 0x61 | Sets reader with ICC communication parameters |
| 0x62 | Turns card power ON |
| 0x63 | Turns card power OFF |
| 0x64 | Sends RESET signal to card |
| 0x65 | Gets reader-card status |
| 0x66 | Sends one byte to reader |
| 0x67 | Sends data block to reader |
| 0x68 | Makes reader resend last data block |
| 0x69 | Gets reader capabilities |
| 0x6A | Deactivate reader |
| 0x6B | Activate reader-dependent features |
| 0x6C-0x6F | Reserved |
Hardware Security
Problems
 All data and passwords on a card are stored in the EEPROM and can be erased or modified by an unusual voltage supply. Therefore some security processors implemented sensors for environmental changes. However, since it is difficult to find the right level of sensitivity and there is a voltage fluctuation when the power is supplied to the card, this method is not widely used. Other successful attacks methods include heating the controller to a high temperature or focusing the UV light on the EEPROM, thus removing the security lock. Invasive physical attacks are the most destructive when the card is cut and processor removed. Then the layout of the chip can be reverse engineered.
All data and passwords on a card are stored in the EEPROM and can be erased or modified by an unusual voltage supply. Therefore some security processors implemented sensors for environmental changes. However, since it is difficult to find the right level of sensitivity and there is a voltage fluctuation when the power is supplied to the card, this method is not widely used. Other successful attacks methods include heating the controller to a high temperature or focusing the UV light on the EEPROM, thus removing the security lock. Invasive physical attacks are the most destructive when the card is cut and processor removed. Then the layout of the chip can be reverse engineered.

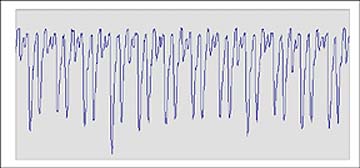 Differential Power Analysis (DPA), is a statistical attack on a cryptographic algorithm which compares an hypothesis with a measured outcome and is often capable of extracting an encryption key from a smart card or other computing device. Simple Power Analysis (SPA), the direct analysis of the recorded power data to determine actions and data, is also useful.
Differential Power Analysis (DPA), is a statistical attack on a cryptographic algorithm which compares an hypothesis with a measured outcome and is often capable of extracting an encryption key from a smart card or other computing device. Simple Power Analysis (SPA), the direct analysis of the recorded power data to determine actions and data, is also useful.
Solutions
Several technologies have been developed to protect Smart Cards. These are technologies of STMicroelectronics against SPA/DPA attacks:
Technology barrier. Advanced 0.6 micron technology greatly reduces the size and power consumption of cards as well as the relative variations in their operating parameters. This makes it very hard for external SPA/DPA methods to distinguish between normal card fluctuations and data-related fluctuations.
Clock fluctuation. A special Clock Software Management facility, when properly used, results in highly variable software timing when the embedded application program is executing.
Unpredictable behavior. A built-in timer with Interrupt capability and an Unpredictable Number Generator is used to impose unpredictable variations on software execution behavior, with consequent changes in the pattern of power consumption.
Robust design. A modular design allows new hardware variations, including custom variations, to be produced quickly and efficiently, thereby allowing fast response to new attack scenarios.
Memory control for multi-applications. An enhanced Memory Access Control system provides secure operating system support for multi-application cards.
Security mechanisms and firmware functions. An enhanced set of security mechanisms and firmware functions allow the application to detect and respond appropriately to the occurrence of conditions that might indicate an attack. These conditions include invalid operating conditions, bad opcodes, bad addresses and violations of chip integrity; the possible responses include interrupts, program reset, immediate erasure of all RAM data and flash programming of the entire EEPROM array.
OS Security
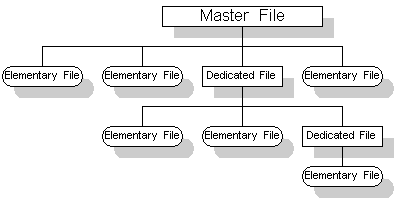 Data on Smart Cards is organized into a tree hierarchy. This has one master file (MF or root) which contains several elementary files (EF) and several dedicated files (DF). DFs and MF correspond to directories and EFs correspond to files, analogous to the hierarchy in any common OS for PCs. However, these two hierarchies differ in that DFs can also contain data. DF's, EF's and MF's header contains security attributes resembling user rights associated with a file/directory in a common OS. Any application can traverse the file tree, but it can only move to a node if it has the appropriate rights.
Data on Smart Cards is organized into a tree hierarchy. This has one master file (MF or root) which contains several elementary files (EF) and several dedicated files (DF). DFs and MF correspond to directories and EFs correspond to files, analogous to the hierarchy in any common OS for PCs. However, these two hierarchies differ in that DFs can also contain data. DF's, EF's and MF's header contains security attributes resembling user rights associated with a file/directory in a common OS. Any application can traverse the file tree, but it can only move to a node if it has the appropriate rights.
Attributes (Access Rights)
There are five basic levels of access rights to a file (both DF and EF). Some OS provide further levels.
Basic levels can be categorized, increasingly in security, as follows:
Always (ALW): Access of the file can be performed without any restriction.
Card holder verification 1 (CHV1): Access can only be possible when a valid CHV1 value is presented.
Card holder verification 2 (CHV2): Access can only be possible when a valid CHV2 value is presented.
Administrative (ADM): Allocation of these levels and the respective requirements for their fulfilment are the responsibility of the appropriate administrative authority.
Never (NEV): Access of the file is forbidden.
However, presenting a CHV2 does not suffice to access a file requiring CHV1. CHV1 and CHV2 correspond to the two security PINs stored in the card: one is a common user identification PIN and the other is a specific unblocking PIN pre-stored in the card.
The PINs
The PINs are stored in separate elementary files, EFCHV1 and EFCHV2 for example. The OS blocks the card after a wrong PIN is entered several consecutive times. The number of times is fixed and depends on the OS. Once blocked, the card can only be unblocked with a specific unblocking PIN stored in the card. The unblocking PIN can become blocked in the same way. If this happens, card is said to be in irreversible blockage and may have to be scrapped for security reasons.
If the PIN is blocked, the attribute of every file is changed to require CHV1. After the unblocking PIN is presented, the file attributes are returned to normal, the counter for the PIN is set back to its maximal value and the counter for the unblocking PIN is decremented. If the latter counter reaches zero, it cannot be used for unblocking the PIN any more. This provides additional security for the card.
Software Security
Software producers also contribute to the Smart Card security - they should provide their products with properly encrypted data and transfers. To help them achieve this goal, hardware-based or OS-based instructions and libraries supporting advanced cryptographic algorithms have been developed.
Conclusions
Most attacks today are classified as class 3 attacks, which means that either the costs associated to break the system are far more than the cost of the system itself, or that the cracker has to spend several or hundred years of computing power to break into a single transaction. Technology is developing faster than cracker methods. Therefore, each new generation of technology usually prevents attacks that the previous generation was vulnerable to.