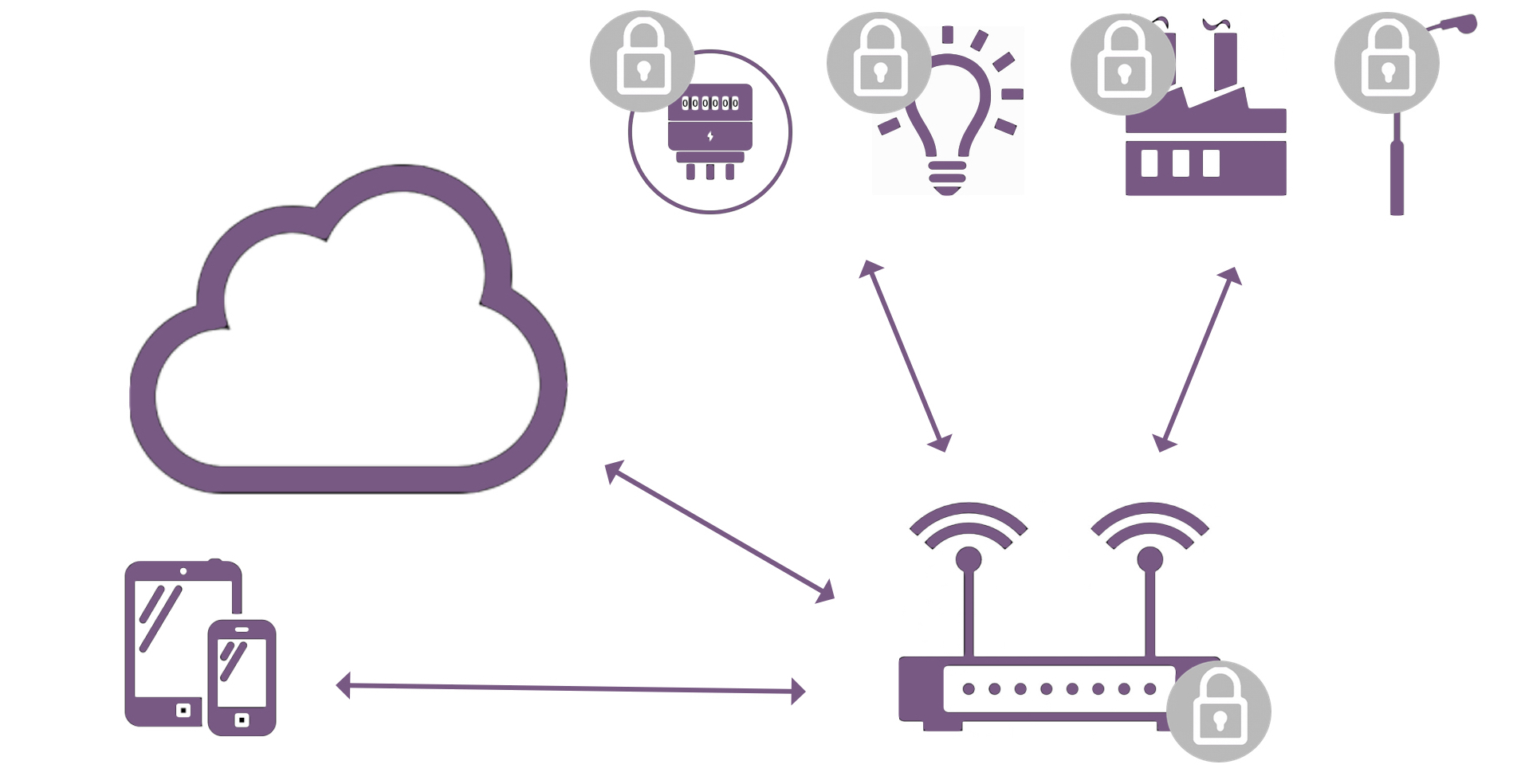
The deployment of Gateways becomes more and more common in IoT and plays a central role, given the limited power resources and connectivity capabilities of a lot of endpoints, but also in response to real-time constraints, implying the need for aggregating control locally over a number of endpoints (unified interface to the user) and implementing automation locally (sensing & control) without constantly communicating with the Cloud.
Gateways can be found in Smart homes (for example to control lighting, to control appliances remotely, door locks, garage openers, collect data from motion or presence sensors, etc.). Other application areas include Industrial automation systems or street lights in smart cities.
These gateways have three types of interfaces:
Interface to the Cloud on one hand (typically through WiFi or cellular)
Interface to local devices (typically using communications standards like ZigBee, Thread, BLE)
Interface to users’ phones and tablets (typically through WiFi or BLE)
The interface to the Cloud is crucial, as it is the interface towards the external world. Therefore, authentication of the remote server it connects to is critical, to make sure a rogue server does not access the gateway with its Private data and functionality, and to insure a door is not opened for an attacker to load a malware on the gateway. But also, authentication of the gateway itself to the Cloud and the service(s) running in the Cloud is essential to protect the Cloud infrastructure, protect access to the services and the associated monetisation, and protect the integrity of data uploaded to the Cloud. As a result, mutual authentication gateway-Cloud is key to secure the IoT applications.
The interface to local devices must be encrypted and authenticated too, to avoid an injection of fake messages, the inclusion of unauthorised devices into the private local network set up by the gateway which could disrupt local automation mechanisms, or the leakage of data that could be captured by sensing tools tens of meters away from the gateway. A challenge is the secure sharing of the network key(s) with new devices to be on-boarded onto the network.
Finally, as user devices like phones are used to pair devices with the gateway or to control it, the gateway will need to implement access control mechanisms to these devices and the apps running on it.
Java Card-based secure elements are a prime choice for implementing gateway security; Java Card being the leading application platform for secure elements, many products are available today for integration into gateway hardware. Java Card based applications can be loaded on the secure element to ensure mutual device / cloud authentication and provide security services to attached devices. Since a Java Card based secure element can be updated with new applications, a service provider can ensure that authentication schemes supported in the device hardware, continue to follow policies set by cloud platforms. This is a unique advantage compared to static hardware security options, which run the risk of being quickly obsoleted, or need to rely on code loaded in unsecured device software to adapt to new security policies.
Additional use cases for Java Card in home and gateway environments can easily be found. oneM2M TR-0038 “Developer Guide: Implementing Security” describes a complete application scenario in a smart home environments, where some components could be advantageously developed using Java Card technology:
A Door Lock applications implemented on top of Secure Components supporting a Java Card Virtual Machine, to ease portability across hardware from different suppliers.
A Mobile Phone application relying on a Java Card applet running inside the SIM card.
New examples of Java Card usage are being rolled up every day, both in home and industrial applications.